Overview
F5 NGINXaaS for Azure (NGINXaaS) enables customers to secure traffic by adding SSL/TLS certificates to a deployment. NGINXaaS can fetch certificates directly from Azure Key Vault, rotate certificates, and provide observability on the status of your certificates.
This document provides details about using SSL/TLS certificates with your F5 NGINXaaS for Azure deployment.
NGINXaaS supports up to 100 TLS/SSL certificates of the following types:
- Self-signed certificates, Domain Validated (DV) certificates, Organization Validated (OV) certificates, and Extended Validation (EV) certificates.
NGINX supports the following certificate formats:
- PEM and PKCS12 format certificates.
Add a certificate from an Azure Key Vault to your NGINXaaS deployment using your preferred client tool:
- Add certificates using the Azure portal
- Add certificates using the Azure CLI
- Add certificates using Terraform
You can overwrite the NGINX default protocol to configure the desired TLS/SSL policy. Read more about the procedure in the Module ngx_http_ssl_module documentation.
You can associate multiple certificates for the same domain; the "ssl_certificate" directive can be specified multiple times to load certificates of different types. To learn more, see the Module ngx_http_ssl_module documentation.
You can also add your certificate as a file to your NGINX configuration filesystem; refer to Upload an NGINX configuration to learn about the different options. Although this is a quick method for adding SSL/TLS certificates to your NGINXaaS deployment, we recommend adding certificates through Azure Key Vault (AKV) for enhanced security, certificate rotation, and monitoring.
Once a certificate has been added, update your NGINX configuration to reference your SSL/TLS certificate and key file paths.
http {
server {
listen 443 ssl;
ssl_certificate /etc/nginx/certs/mycert.cert;
ssl_certificate_key /etc/nginx/certs/mycert.key;
# ...
}
}NGINXaaS for Azure regularly polls the AKV to check if the certificate has been updated. If an updated certificate is found, it is automatically rotated on the deployment within 4 hours. Any change to the NGINX configuration will trigger all SSL/TLS certificates to be rotated immediately.
For Azure client tools, such as the Azure CLI or Azure Resource Manager, the certificate is referenced from AKV using its Key Vault secret identifier. If the secret identifier specifies a version, NGINXaaS will not rotate the certificate. To enable certificate rotation, ensure the secret id does not contain a version, for example, https://myvault.vault.azure.net/secrets/mysecret. Certificates added using the Azure Portal will automatically be rotated.
WarningIf any of your SSL/TLS certificates or your NGINX configuration has issues, the certificates will not be rotated.
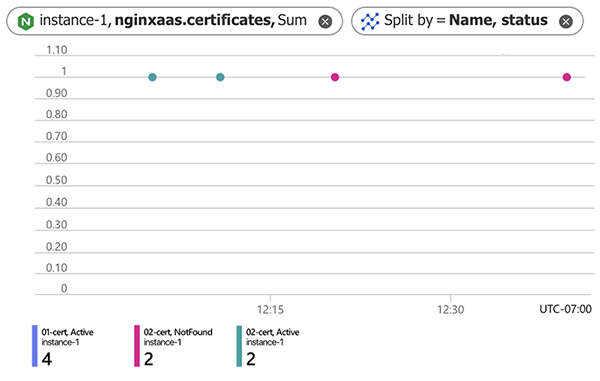
To view the status of your SSL/TLS certificates, enable monitoring for your NGINXaaS deployment and navigate to the Metrics tab in the Azure portal. View the nginxaas.certificates metric under the nginxaas statistics metric namespace. The nginxaas.certificates metric allows you to filter by certificate name and the status of the certificate. The status dimension reports the health of your certificates through the following values:
| Status | Description |
|---|---|
active |
The certificate was successfully fetched from AKV. |
unauthorized |
Azure returned a 401/403 error when fetching the certificate from AKV, which usually indicates an issue with the deployment’s Managed Identity. |
not found |
Azure returned a 404 error when fetching the certificate from AKV. |
incompatible |
An error occurred while fetching or processing the certificate from AKV. The possible reasons include:
|
The following section describes common errors you might encounter while adding SSL/TLS certificates to your NGINXaaS deployment and how to resolve them.
Common certificate errors
Description: The Managed Identity associated with the NGINXaaS deployment does not have permissions to fetch certificates from key vault. This error is returned when the key vault’s permission model is set to Azure role-based access control.
Resolution: Assign the Key Vault Secrets User role to the managed identity associated with your NGINXaaS deployment.
Create a role assignment using the CLI
-
Get the principal ID of the user or system assigned managed identity.
-
User assigned managed identity
Set the following environment variables before copying the below Azure CLI command.
MI_NAME: the name of the managed identityMI_RESOURCE_GROUP: the name of the resource group the managed identity is in
shell mi_principal_id=$(az identity show --name $MI_NAME \ --resource-group $MI_RESOURCE_GROUP \ --query principalId --output tsv) -
System assigned managed identity
Set the following environment variables before copying the below Azure CLI command.
DEP_NAME: the name of the NGINXaaS deploymentDEP_RESOURCE_GROUP: the name of the resource group the NGINXaaS deployment is in
shell mi_principal_id=$(az nginx deployment show --name $DEP_NAME \ --resource-group $DEP_RESOURCE_GROUP \ --query identity.principalId --output tsv)
-
-
Get the resource ID of the key vault.
Set the following environment variables before copying the below Azure CLI command.
KV_NAME: the name of the key vaultKV_RESOURCE_GROUP: the name of the resource group the key vault is in
shell key_vault_id=$(az keyvault show --name $KV_NAME \ --resource-group $KV_RESOURCE_GROUP \ --query id --output tsv) -
Create the role assignment.
shell az role assignment create --assignee $mi_principal_id \ --role "Key Vault Secrets User" \ --scope $key_vault_id
Description: The Managed Identity associated with the NGINXaaS deployment has not been assigned to an access policy on the key vault. This error is returned when the key vault’s permission model is set to Vault access policy.
Resolution: Assign an access policy to the managed identity associated with your NGINXaaS deployment with Get secrets permissions or higher. If you are using the Azure portal, assign an additional access policy to your user with List certificates permissions or higher.
Create an access policy using the CLI
-
Get the principal ID of the user or system assigned managed identity.
-
User assigned managed identity
Set the following environment variables before copying the below Azure CLI command.
MI_NAME: the name of the managed identityMI_RESOURCE_GROUP: the name of the resource group the managed identity is in
shell mi_principal_id=$(az identity show --name $MI_NAME \ --resource-group $MI_RESOURCE_GROUP \ --query principalId --output tsv) -
System assigned managed identity
Set the following environment variables before copying the below Azure CLI command.
DEP_NAME: the name of the NGINXaaS deploymentDEP_RESOURCE_GROUP: the name of the resource group the NGINXaaS deployment is in
shell mi_principal_id=$(az nginx deployment show --name $DEP_NAME \ --resource-group $DEP_RESOURCE_GROUP \ --query identity.principalId --output tsv)
-
-
Create the access policy.
Set the following environment variables before copying the below Azure CLI command.
KV_NAME: the name of the key vaultKV_RESOURCE_GROUP: the name of the resource group the key vault is in
shell az keyvault set-policy --name $KV_NAME \ --resource-group $KV_RESOURCE_GROUP \ --object-id $mi_principal_id \ --secret-permissions get
Description: The key vault’s firewall is enabled and NGINXaaS is not authorized to fetch certificates.
Resolution:
Allow NGINXaaS to access the key vault through one of these mechanisms:
- Configure Network Security Perimeter to allow the subscription of the NGINXaaS deployment to access the key vault.
Create a network security perimeter using the CLI
-
Create a network security perimeter.
Set the following environment variables before copying the below Azure CLI command.
NSP_NAME: the name of the network security perimeterNSP_RESOURCE_GROUP: the name of the resource group the network security perimeter will be in
az network perimeter create --name $NSP_NAME --resource-group $NSP_RESOURCE_GROUP -
Create a profile for the network security perimeter.
Set the following environment variable is set before copying the below Azure CLI command.
PROFILE_NAME: the name of the network security perimeter profile
shell az network perimeter profile create --name $PROFILE_NAME \ --resource-group $NSP_RESOURCE_GROUP \ --perimeter-name $NSP_NAME -
Get the resource ID of the key vault.
Set the following environment variables before copying the below Azure CLI command.
KV_NAME: the name of the key vaultKV_RESOURCE_GROUP: the name of the resource group the key vault is in
shell key_vault_id=$(az keyvault show --name $KV_NAME \ --resource-group $KV_RESOURCE_GROUP \ --query id --output tsv) -
Get the resource ID of the network security profile.
shell nsp_profile_id=$(az network perimeter profile show --name $PROFILE_NAME \ --resource-group $NSP_RESOURCE_GROUP \ --perimeter-name $NSP_NAME --query id --output tsv) -
Associate the key vault with the network security perimeter
shell az network perimeter association create --name key-vault-association \ --perimeter-name $NSP_NAME \ --resource-group $NSP_RESOURCE_GROUP \ --private-link-resource "{id:$key_vault_id}" \ --profile "{id:$nsp_profile_id}" -
Add an inbound access rule to allow the NGINXaaS deployment’s subscription.
Set the following environment variables before copying the below Azure CLI command.
RULE_NAME: the name of the access ruleDEP_SUBSCRIPTION_ID: the subscription ID of the NGINXaaS deployment
shell az network perimeter profile access-rule create --name $RULE_NAME \ --profile-name $PROFILE_NAME \ --perimeter-name $NSP_NAME \ --resource-group $NSP_RESOURCE_GROUP \ --subscriptions [0].id="/subscriptions/$DEP_SUBSCRIPTION_ID"
- Integrate with a Private Endpoint to allow NGINXaaS to fetch certificates via Azure Private Link.
Create a private link using the CLI
-
Get the resource ID of the key vault.
Set the following environment variables before copying the below Azure CLI command.
KV_NAME: the name of the key vaultKV_RESOURCE_GROUP: the name of tshe resource group the key vault is in
shell key_vault_id=$(az keyvault show --name $KV_NAME \ --resource-group $KV_RESOURCE_GROUP \ --query id --output tsv) -
Create a private endpoint.
Set the following environment variables before copying the below Azure CLI command.
PE_NAME: the name of the private endpointPE_RESOURCE_GROUP: the name of the resource group the private endpoint will be inVNET_NAME: the name of the virtual network that is delegated to NGINXaaSVNET_RESOURCE_GROUP: the name of the resource group the virtual network is inSUBNET_NAME: the name of the subnet for private endpointsPE_CONNECTION_NAME: the name of the private endpoint connectionLOCATION: the location of the virtual network
shell az network private-endpoint create --name $PE_NAME \ --resource-group $PE_RESOURCE_GROUP \ --vnet-name $VNET_NAME \ --subnet $SUBNET_NAME \ --private-connection-resource-id $key_vault_id \ --group-id vault \ --connection-name $PE_CONNECTION_NAME \ --location $LOCATION -
Create a private DNS zone and link VNet.
Set the following environment variables before copying the below Azure CLI command.
ZONE_RESOURCE_GROUP: the name of the resource group for the DNS zoneZONE_NAME: the name of the DNS zoneDNS_LINK_NAME: the name of the DNS zone link
shell vnet_id=$(az network vnet show --name $VNET_NAME \ --resource-group $VNET_RESOURCE_GROUP \ --query id --output tsv)shell az network private-dns zone create --resource-group $ZONE_RESOURCE_GROUP \ --name $ZONE_NAME az network private-dns link vnet create --resource-group $ZONE_RESOURCE_GROUP \ --zone-name $ZONE_NAME \ --name $DNS_LINK_NAME \ --virtual-network $vnet_id \ --registration-enabled false -
Add DNS zone group to the private endpoint.
Set the following environment variables before copying the below Azure CLI command.
DNS_ZONE_GROUP_NAME: the name of the resource group for the DNS zone
shell az network private-endpoint dns-zone-group create \ --resource-group $PE_RESOURCE_GROUP \ --endpoint-name $PE_NAME \ --name $DNS_ZONE_GROUP_NAME \ --private-dns-zone $ZONE_NAME \ --zone-name $ZONE_NAME
- Allow access from Virtual Network delegated to NGINXaaS.
Allow Virtual Network access using the CLI
-
Get the resource ID of the virtual network.
Set the following environment variables before copying the below Azure CLI command.
VNET_NAME: the name of the virtual network that is delegated to NGINXaaSVNET_RESOURCE_GROUP: the name of the resource group the virtual network is in
shell vnet_id=$(az network vnet show --name $VNET_NAME \ --resource-group $VNET_RESOURCE_GROUP \ --query id --output tsv) -
Get the resource ID of the subnet.
Set the following environment variable before copying the below Azure CLI command.
SUBNET_NAME: the name of the subnet that is delegated to NGINXaaS
shell subnet_id=$(az network vnet subnet show --name $SUBNET_NAME \ --vnet-name $VNET_NAME \ --resource-group $VNET_RESOURCE_GROUP \ --query id --output tsv) -
Add the virtual network rule to the key vault.
Set the following environment variables before copying the below Azure CLI command.
KV_NAME: the name of the key vaultKV_RESOURCE_GROUP: the name of the resource group the key vault is in
shell az keyvault network-rule add --name $KV_NAME \ --resource-group $KV_RESOURCE_GROUP \ --subnet $subnet_id
Ensure that the Network Security Group on the subnet delegated to the NGINXaaS deployment allows outbound traffic to the internet
Description: Another operation on this, or a dependent resource, is in progress.
Resolution: Retry the operation after the current operation reaches a terminal state.
Description: The certificate’s key vault secret ID was not found in the key vault.
Resolution: Ensure the specified key vault secret ID exists and has the correct format, for example, https://myvault.vault.azure.net/secrets/abcd/v1.
Description: The certificate being deleted or modified is referenced in the NGINX configuration. The attempted modification would prevent the NGINX config from being applied.
Resolution: Remove references to the certificate in the NGINX config, or add a new certificate resource to the NGINXaaS deployment with the modified certificate and key paths.
Description: The Managed Identity associated with the NGINXaaS deployment does not have permissions to fetch certificates from key vault. This error is returned when the key vault’s permission model is set to Vault access policy.
Resolution: Assign an access policy to the managed identity associated with your NGINXaaS deployment with Get secrets permissions or higher. If you are using the Azure portal, assign an additional access policy to your user with List certificates permissions or higher.
Create an access policy using the CLI
-
Get the principal ID of the user or system assigned managed identity.
-
User assigned managed identity
Set the following environment variables before copying the below Azure CLI command.
MI_NAME: the name of the managed identityMI_RESOURCE_GROUP: the name of the resource group the managed identity is in
shell mi_principal_id=$(az identity show --name $MI_NAME \ --resource-group $MI_RESOURCE_GROUP \ --query principalId --output tsv) -
System assigned managed identity
Set the following environment variables before copying the below Azure CLI command.
DEP_NAME: the name of the NGINXaaS deploymentDEP_RESOURCE_GROUP: the name of the resource group the NGINXaaS deployment is in
shell mi_principal_id=$(az nginx deployment show --name $DEP_NAME \ --resource-group $DEP_RESOURCE_GROUP \ --query identity.principalId --output tsv)
-
-
Create the access policy.
Set the following environment variables before copying the below Azure CLI command.
KV_NAME: the name of the key vaultKV_RESOURCE_GROUP: the name of the resource group the key vault is in
shell az keyvault set-policy --name $KV_NAME \ --resource-group $KV_RESOURCE_GROUP \ --object-id $mi_principal_id \ --secret-permissions get
Description: A file already exists on the instance’s filesystem with the certificate or key’s file path.
Resolution: Rename the certificate or key path, so there are no collisions with existing certificate and NGINX config file paths.
Description: The certificate is set to disabled in the key vault.
Resolution: Enable the certificate in the key vault.
Enable a certificate in the key vault using the CLI
-
Get the resource ID of the certificate.
Set the following environment variables before copying the below Azure CLI command.
CERT_NAME: the name of the certificateKV_NAME: the name of the key vault
shell certificate_id=$(az keyvault certificate show --name $CERT_NAME \ --vault-name $KV_NAME \ --query id --output tsv) -
Enable the certificate.
az keyvault certificate set-attributes --enabled true --id $certificate_id
Description: No certificate was found when parsing the file.
Resolution: Ensure the file is not empty and contains properly formatted PEM or PKCS12 certificate data.
Description: The retrieved secret is missing the contentType field.
Resolution: When creating an Azure certificate in key vault, the contentType field will be properly set to either application/x-pem-file or application/x-pkcs12. If a certificate is added as a generic Azure secret the contentType field must be manually set to help with interpreting the secret data when it is retrieved. We recommend creating a certificate object, instead of a secret object containing certificate data, to ensure proprer formatting and contentType.
Description: The retrieved secret’s content type, as interpreted from the contentType field, is of an unsupported type.
Resolution: When creating an Azure certificate in key vault, the contentType field will be properly set to either application/x-pem-file or application/x-pkcs12. NGINXaaS does not support other content types added as generic Azure secrets. Ensure the provided certificate is either a PEM or PKCS12 Azure certificate.
Description: The PKCS12 certificate could not be parsed.
Resolution: Ensure the file is not empty and contains properly formatted PKCS12 certificate data.
Description: The PEM certificate could not be parsed.
Resolution: Ensure the file is not empty and contains properly formatted PEM certificate data.