Microsoft Entra: Set up OIDC authentication
This guide explains how to configure Microsoft Entra (AD) as an identity provider (IdP) for F5 NGINX Instance Manager. By implementing OIDC for authentication, administrators can simplify user management in NGINX Instance Manager. Instead of creating and managing users individually, administrators can create user groups in NGINX Instance Manager that align with groups in their Identity Provider. Access and permissions for users are determined by the roles assigned to their respective user groups. Users from the Identity Provider who are not part of a group with an assigned role will not have access to NGINX Instance Manager.
We strongly recommend Open ID Connect (OIDC) as the preferred authentication method for the NGINX Instance Manager. OIDC brings several benefits, including Single Sign-On (SSO) and simplified user management through user groups.
To configure Microsoft Entra as an OIDC IdP, follow these steps:
Configure Microsoft Entra:
- Create an Application Registration for NGINX Instance Manager.
- Add owners (users) and their email addresses to Microsoft Entra.
- Create groups in Microsoft Entra and assign user membership.
Configure NGINX Instance Manager:
- Add user groups to NGINX Instance Manager, using the same group names as in Microsoft Entra.
- Configure NGINX Plus in NGINX Instance Manager to use Microsoft Entra as the designated identity provider.
To successfully follow the instructions in this guide, you must complete the following requirements:
- Create a Microsoft Entra premium account. If you have a standard account, you’ll need to upgrade.
- Install Instance Manager on a server that also has NGINX Plus R25 or a newer version installed. Make sure the server hosting NGINX Plus has a fully qualified domain name (FQDN).
- Install the NGINX JavaScript module (njs) on the same server as Instance Manager. This module is necessary for managing communications between NGINX Plus and the identity provider.
Complete the steps in the section to configure Microsoft Entra for use with NGINX Instance Manager.
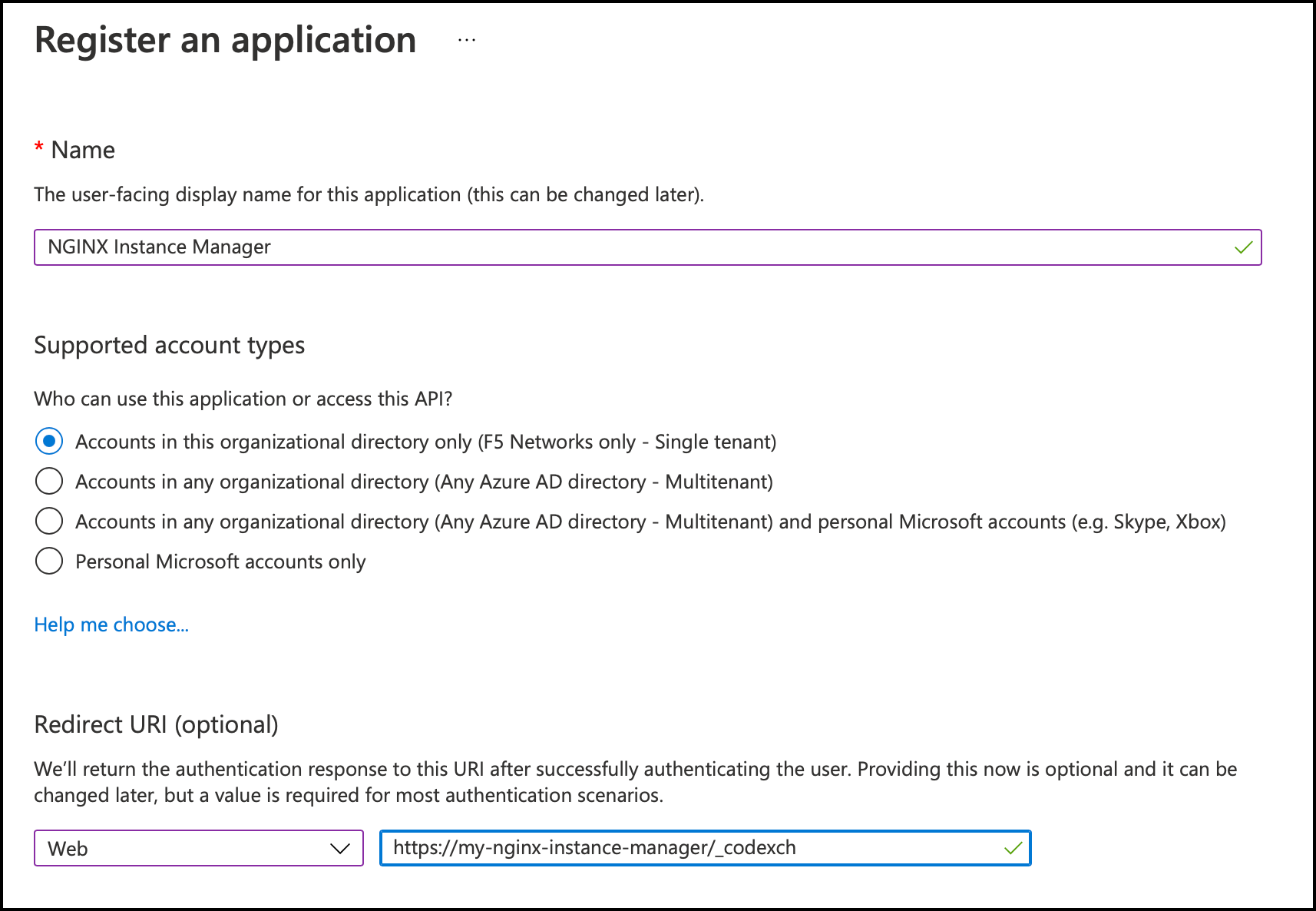
To register an application with Microsoft Entra:
-
Go to the Azure portal and log in.
-
Select Microsoft Entra from the list of Azure services.
-
On the left navigation menu, under the Manage section, select App registrations.
-
Select New registration.
-
Provide the following details:
- Enter a name for the application in the Name field, such as "NGINX Instance Manager".
- Select Account in this organizational directory only from the list of account types.
- Under the Redirect URI section, choose Web and enter the redirect URI, for example,
https://<my-nginx-instance-manager>/_codexch.
-
Select Register.
-
On the confirmation page, make a note of the following information. You’ll need to provide this information later to complete the setup:
- Application (client) ID
- Directory (tenant) ID
ImportantMake sure to save the value of the client secret in a secure location for future reference. Once you navigate away from the page, the value cannot be retrieved again.
To create a client secret:
- On the left navigation menu, under the Manage section, select Certificates & secrets.
- Select New client secret.
- In the Description box, type a description for the client secret.
- Select Add. The client secret will be added to the list with a unique secret string value and ID.
- Copy the value for the client secret.
ImportantMake sure to add at least one user with administrative privileges. Failure to do so may lock admin users out of NGINX Instance Manager. If that happens, revert to Basic Auth to restore access.
To add owners (users):
- On the left navigation menu, under the Manage section, select Owners.
- Select Add owners.
- Search for the user you want to add, then select Select. Repeat this step for each user you want to add.
The only supported group claim format for groups created in Microsoft Entra is Microsoft Entra group ObjectId.
To include the user’s group membership information in the token for authentication and authorization, follow these steps:
- On the left navigation menu, under the Manage section, select Token configuration.
- Select Add groups claim.
- Select Groups assigned to the application.
- Select Add.
By default, tokens expire after 60 minutes. You can find instructions on configuring token expiration in the Microsoft Entra topic Configurable token lifetime properties.
Adding a group to the registered application will give all group members the same access.
- On the left navigation menu, under the Manage section, select Overview.
- In the Essentials section, select the link next to Managed application in local directory.
- In the Getting Started section, select Assign users and groups.
- Select Add user/group.
- On the Add Assignment form, under the Users and groups section, select None Selected.
- In the search box in the Users and groups drawer, type the name of the group you want to associate with the application.
- Select the group from the list, and select Select.
- Finally, select Assign.
Roles in NGINX Instance Manager are a critical part of role-based access control (RBAC). By creating roles, you define the access levels and permissions for different user groups that correspond to groups in your Identity Provider (IdP).
NGINX Instance Manager comes pre-configured with an administrator role called admin. Additional roles can be created as needed.
The admin user or any user with CREATE permission for the User Management feature can create a role.
Follow these steps to create a role and set its permissions:
-
In a web browser, go to the FQDN for your NGINX Instance Manager host and log in.
-
Select the Settings (gear) icon in the upper-right corner.
-
From the left navigation menu, select Roles.
-
Select Create.
-
On the Create Role form, provide the following details:
- Name: The name to use for the role.
- Display Name: An optional, user-friendly name to show for the role.
- Description: An optional, brief description of the role.
-
To add permissions:
- Select Add Permission.
- Choose the NGINX Instance Manager module you’re creating the permission for from the Module list.
- Select the feature you’re granting permission for from the Feature list. To learn more about features, refer to Get started with RBAC.
- Select Add Additional Access to choose a CRUD (Create, Read, Update, Delete) access level.
- Choose the access level(s) you want to grant from the Access list.
- Select Save.
-
Repeat step 6 if you need to add more permissions for other features.
-
When you’ve added all the necessary permissions, select Save to create the role.
Suppose you need to create an "app-developer" role. This role allows users to create and edit applications but not delete them or perform administrative tasks. You would name the role app-developer, select the relevant features, and grant permissions that align with the application development process while restricting administrative functions.
Group names must match with your IdPTo ensure that NGINX Instance Manager and your IdP work together seamlessly, group names must exactly match between the two systems. If the group names don’t match, the OIDC integration will fail, preventing users from accessing NGINX Instance Manager. For example, if you have a group called "app-developers" in your IdP, you must create a user group called "app-developers" in NGINX Instance Manager. The group claim must also be part of the token your IdP generates. Refer to your IdP’s documentation for guidance on adding group claims.
Here’s how to create a user group and assign roles:
-
In a web browser, go to the FQDN for your NGINX Instance Manager host and log in.
-
Select the Settings (gear) icon in the upper-right corner.
-
From the left navigation menu, select User Groups.
-
Select Create.
-
On the Create Group form, provide the following information:
- Group Name (required): The group name or Object ID. This must exactly match the name used in the IdP.
- Display Name: A friendly name for the group.
- Description: A brief description of the group.
-
Select one or more roles from the Roles list to assign to the group.
ImportantAt least one user group must have theadminrole assigned. -
Select Save to create the group.
Imagine you’ve created a role called "app-developer" for users who develop, create, and modify applications but don’t need to perform administrative tasks. You want this role to correspond to a group in your IdP named "app-developers."
In this case, select the "app-developer" role when creating the "app-developers" user group in NGINX Instance Manager. Users in the "app-developers" group from the IdP will inherit the "app-developer" role in NGINX Instance Manager.
Configure NGINX Plus to use Microsoft Entra as the identity provider.
-
Install the NGINX JavaScript module (njs) on your NGINX Instance Manager server by running the appropriate command. This module is required for handling the interaction between NGINX Plus and Microsoft Entra (IdP).
-
CentOS, RHEL:
sudo yum install nginx-plus-module-njs -
Debian, Ubuntu:
sudo apt install nginx-plus-module-njs
-
-
Open the
/etc/nginx/nginx.conffile in a text editor and add the following directive to the top-level ("main") section to load the NGINX JavaScript module:load_module modules/ngx_http_js_module.so; -
Open the
/etc/nms/nginx/oidc/openid_configuration.conffile in a text editor. Replace the following variables in the file with the values you saved when configuring Microsoft Entra. Save the changes:{client_key}: Replace with the Application (client) ID obtained when registering the application.{tenant_key}: Replace with the Directory (tenant) ID obtained when registering the application.{client_secret}: Replace with the encoded client secret that was generated when creating the client secret.
Example openid_configuration.conf
```yaml # NGINX Instance Manager - OpenID Connect configuration # Created for v. 2.0 # (c) NGINX, Inc. 2021 # Enable when using OIDC with Microsoft Entra map $http_authorization $groups_claim { "~^Bearer.*" $jwt_claim_roles; default $jwt_claim_groups; } map $jwt_audience $jwt_aud_client { default $jwt_audience; ~^api://(.+)$ $1; } map $http_authorization $user_email { "~^Bearer.*" '$jwt_aud_client@$oidc_domain'; default $jwt_claim_email; } map $host $oidc_authz_endpoint { default "https://login.microsoftonline.com/{tenant_key}/oauth2/v2.0/authorize"; } map $host $oidc_token_endpoint { default "https://login.microsoftonline.com/{tenant_key}/oauth2/v2.0/token"; } map $host $oidc_jwt_keyfile { default "https://login.microsoftonline.com/{tenant_key}/discovery/v2.0/keys"; } ``` -
Using a text editor, open the
/etc/nginx/conf.d/nms-http.confconfiguration file and uncomment the OIDC settings starting with#OIDC. Comment out the Basic Authentication settings. Save the changes.Example nms-http.conf
```yaml # NGINX Instance Manager - Instance Manager configuration # Created for v. 2.0 # (c) NGINX, Inc. 2021 # OIDC: use email as a unique identifier proxy_set_header Nginx-Management-Suite-User $user_email; proxy_set_header Nginx-Management-Suite-Groups $groups_claim; proxy_set_header Nginx-Management-Suite-ExternalId $jwt_claim_sub; # OIDC authentication include /etc/nms/nginx/oidc/openid_connect.conf; ``` -
Verify that the configuration file does not contain any errors:
sudo nginx -t -
Reload NGINX and apply the configuration:
sudo nginx -s reload
- Open a web browser and go to the FQDN of your NGINX Instance Manager host. You will be redirected to the Microsoft Entra login page.
- Enter your Microsoft Entra email address and password to log in.